What is an IoT protocol?
An IoT protocol is a communication system for exchanging data between connected objects. These protocols define the rules for establishing connections, transferring data and guaranteeing the security and reliability of IoT networks.
Furthermore, the IoT Protocol is not limited to communication protocols; it also includes standards for device management, data processing and interoperability. By adhering to these standards, IoT developers can create robust, scalable solutions that can adapt to ever-changing technological landscapes.

IoT Protocol architecture
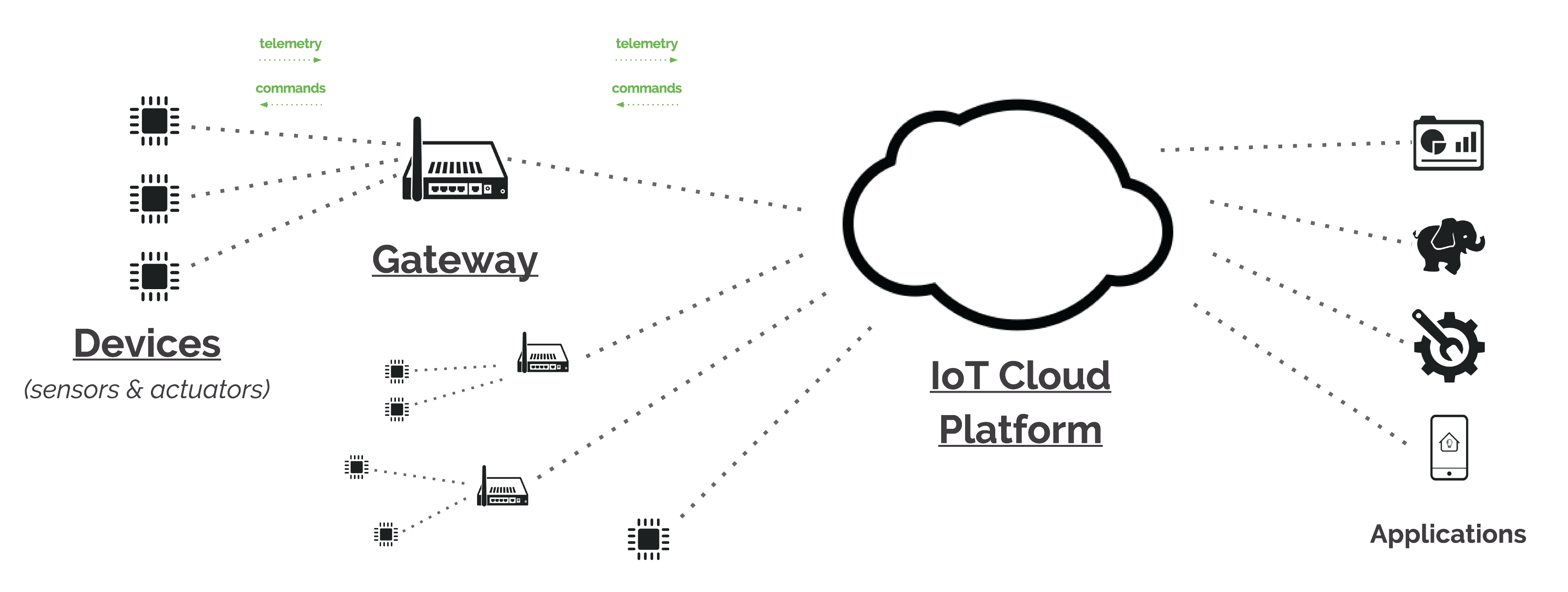
The IoT Protocol architecture comprises three main components: the peripheral devices, the gateway and the Cloud infrastructure. Each component plays a crucial role in the overall operation of the IoT system.
Peripheral devices
Also known as IoT nodes, are the physical devices that collect and generate data. They can be sensors, actuators or any other IoT-enabled device. These devices are equipped with advanced sensors and processors that enable them to capture and process data in real time.
Gateway
It acts as a bridge between peripheral devices and the cloud infrastructure. It collects, filters and processes data from peripheral devices before transmitting it to the cloud infrastructure. The gateway plays an essential role in ensuring that only relevant, high-quality data is transmitted, thus optimizing the use of network resources.
The cloud infrastructure is where data collected by peripheral devices is stored, processed and analyzed. It provides the resources and services needed to facilitate data management, storage and analysis.
Cloud Plateform
It is designed to handle large volumes of data and perform complex analytical tasks, enabling organizations to gain valuable insights and make data-driven decisions.
The different IoT protocols
There are several protocols used in IoT, each with its own strengths and weaknesses. Understanding the different protocols is essential to choosing the right one for your IoT project.
The main types of protocols are IoT transport protocols and IoT messaging protocols.
IoT transport protocols
IoT transport protocols are responsible for transmitting data between connected objects and servers. They guarantee reliable data delivery, managing packet loss, message sequence and quality of service. They play a crucial role in the Internet of Things, ensuring smooth, secure communication. Among the most widely used transport protocols is MQTT (Message Queuing Telemetry Transport), widely adopted for its lightness and reliability. This protocol is ideal for applications requiring low power consumption and limited bandwidth.
IoT messaging protocols
IoT messaging protocols are used to exchange information between connected objects. They define data formats, encoding rules and compression methods to enable efficient, secure communication between devices.
In addition to transport protocols, IoT messaging protocols are essential to ensure consistent, interoperable communication between the various connected devices. Among these protocols, CoAP (Constrained Application Protocol) stands out for its simplicity and efficiency in resource-constrained environments. It is widely used in sensor networks and applications requiring low power consumption.
It’s important to remember that not all protocols offer the same guarantees of operation in all geographical areas. The choice of protocol can therefore determine the commercial success of a product in certain parts of the world.
For example, LoRaWAN (Long Range Wide Area Network) may be a good solution for use in France, but this may vary in other countries, and even in certain regions. Like the 26 states that make up Brazil, not all will support the same protocols. So it’s strategic to choose the right protocol for the regions where you want to market and operate your product.
The 3 pillars of communication between connected objects: Connectivity, Protocol and Security
🌐 #1 Connectivity
Short range (Bluetooth Low Energy, WiFi, Z-Wave, ZigBee, RFID…), long range and low power consumption (LPWAN: LoRaWAN® or SigFox) or long cellular range (2G, 3G, 4G, LTE-M, NB-IoT, 5G)
👨💻 #2 Protocol
SMS (simple and widely used), MQTT (predominant standard for exchanging messages with a flexible publishing and subscription mechanism) or CoAP / LightweightM2M (LwM2M) minimizing the volumes exchanged and therefore overall energy consumption.
🔒 #3 Security
Common security risks in the IoT protocol include unauthorized access, data breaches, device tampering and malicious attacks. These threats can have serious consequences, ranging from privacy violations to physical damage. To manage object authentication and communication encryption, protocols such as TLS, DTLS and/or OSCore, among others, can be used.

What are the trends in IoT protocols?
In the HBAS (Home and Building Automation Systems) sector, manufacturers tend to turn to WIFI and Zigbee networks. But more and more players are taking an interest in the features of Matter: a very recent open protocol, which is tending to become a new universal standard supported by the GAFAs (Google, Apple, Amazon, etc.). As for the LoRa and Wirepas protocols, they are frequently chosen to design connected applications for the Smart City to optimize energy management, particularly for street lighting. 5G will be used for high data rates, particularly in industry 4.0 and autonomous vehicles.
It should be stressed that the trend is towards standardization of all these protocols. In the years to come, cellular will certainly maintain its unrivalled lead in the mobility market and its position as the favorite. As for Zigbee in the HBAS sector, it could be replaced by Matter, due to the latter’s performance in terms of interoperability and data security.
What expertise does IMPULSE, LACROIX’s design center, offer?
🔎 #1 Identify the protocols best suited to your needs
Our expertise enables us to guide your choice according to the functionalities you require. We master all the main existing protocols and train in the most innovative ones, giving preference to open protocols so as not to limit ourselves to a single manufacturer and facilitate the interoperability of connected equipment.
As a result, the criteria for choosing a protocol must be linked first and foremost to geographical coverage, but also to the product’s durability, and the quantity and nature of the data to be transmitted. In some cases, our expertise may lead us to recommend a protocol other than the one initially chosen by the customer.
👨💻 #2 Working with you to define the best compromise for your product
When it comes to IoT protocols, there are several possibilities. The choice remains yours but must be made with a prior understanding of the benefits and constraints of each solution.
Choosing a more recent protocol will enable higher data throughput, but this performance will often have the disadvantage of increasing your product’s energy consumption, with a predictable impact on its autonomy. Conversely, an older protocol may have the advantage of extending your product’s geographical coverage, while offering greater autonomy.
The choice of MoDem also determines the compatibility of the chosen protocol. To optimize the price of your MoDem, it may be preferable to choose one of the latest generations, which will have the advantage of being more economical, but the disadvantage of no longer supporting older cellular protocols such as 2G.
Contact our experts
The right IoT protocol for your project is not necessarily the latest, the cheapest or the most efficient. However, it must take into account the long-term dimension of the product and be oriented towards the most sober solution possible. It’s best to be accompanied by experts before making your choice, so you can make the best trade-offs according to your strategic objectives.